728x90
1. 디지털 포렌식
디지털포렌식이란?
: Digital + Forensic = 디지털 범죄의 부검
→ 디지털 증거물(스마트폰, PC)을 수집, 분석하여 범죄의 단서와 증거를 찾아내는 과학수사 기법
디지털 포렌식의 대상
- 디스크 포렌식: 컴퓨터 디스크(윈도우, 리눅스, MacOS/개인, 서버, 클라우드)
- 메모리 포렌식: 컴퓨터 메모리(RAM)
- 네트워크 포렌식: 네트워크 패킷, 네트워크 장비 로그, 네트워크 관련 설정들
- 모바일 포렌식: 모바일 디바이스(저장소, 메모리)/IoT 디바이스
- 기타: 데이터베이스 포렌식, 암호 포렌식, 회계 포렌식, 소스코드 포렌식 등
디지털포렌식 5대 원칙
- 정당성의 원칙: 디지털 증거는 법적 절차에 의해 수집되어야 한다. 위법한 방법으로 수집 시 법적 효력이 상실한다.
- 무결성의 원칙: 디지털 증거는 습득 후 어떠한 일이 발생하여도 변조가 되어서는 안 된다.
- 연계성의 원칙: 디지털 증거의 습득, 이송, 분석, 보간, 법정 제출 각 단계에서 담당자와 업무자를 명확히 하여야 한다.
- 신속성의 원칙: 모든 과정은 지체 없이 신속하게 진행되어야 한다.
- 재현의 원칙: 피해 직전과 같은 환경에서 현장 재현 시 피해 당시와 동일한 결과가 나와야 한다.
디지털포렌식의 유형

디지털포렌식의 절차

2. 스테가노그래피
스테가노그래피란?
: Steganography = Stegano(감춰진) + Graphy(글) = 감춰진 글
전달하려는 기밀 정보를 다른 파일, 메시지, 이미지 또는 비디오 안에 숨기는 심층 암호 기술
스테가노그래피의 종류
- Text Steganography: 텍스트 파일에 다른 파일을 숨기는 기술
- Format based method: 텍스트 파일 확장자 변환
- random and statistical generation
- linguistic method
- Audio Steganography: 비트스트림으로 치환될 수 있는 secret message를 오디오 파일에 삽입하는 기술(어려움)
- WAV/AU/MP3 등의 확장자 사용
- Least Siginificant Bit Encoding
- Parity Encoding
- Phase Coding
- Spread Spectrum
- WAV/AU/MP3 등의 확장자 사용
- Image Steganography: 이미지를 다른 파일을 숨기기 위한 수단으로 사용하는 기술(가장 흔하게 사용)
- Least Significant Bit(LSB) Insertion
- Masking and Filtering
- Redundant Pattern Encoding
- Encrypt and Scatter
- Coding and Cosine Transformation
- Network Steganography
- Video Steganography: 디지털 비디오 형식에 다른 파일을 숨기는 기술(Image + Audio Steganography)
- Embedding data in uncompressed raw video and compressing it later
- Embedding data directly into the compressed data stream
- Email Steganography
이미지의 변조 - Bit Pland
- 적절한 연산 방식으로 특정 bit를 수정하여 이미지에 비밀 정보를 삽입
- LSB 변조 방식이 대표적



3. 파일 시그니처
파일 시그니처란?
: 컴퓨터는 파일 이름과 파일 확장자(extension)를 통해 파일 종류를 식별한다.
- 파일 형식마다 가지고 있는 고유의 특징
- 형식마다 특정한 byte값이 정해져 있다.
- 효율적인 식별을 위해 파일 포맷을 구분하고, 특정 위치의 고유 정보를 이용한다.
- 파일 포맷별로 jpeg, gif, doc, ppt 등 고유한 포맷을 가진다.
- 파일의 시작과 끝에 배치된 특정 바이트들의 고유한 값 도는 정보가 정해져 있다.
- header & footer signature
파일 시그니처 분석 이유
- 효율성: 파일의 확장자가 진짜인지를 확인하기 위함
- 헤더와 푸터 시그니처가 다른 형식일 경우 파일에 문제가 있거나 조작된 파일일 가능성이 존재한다.
- 육안으로 확인할 수 없게 은폐된 파일의 존재 여부를 확인할 수 있다.
http://forensic-proof.com/archives/300
파일 시그니처 모음 (Common File Signatures) | FORENSIC-PROOF
forensic-proof.com

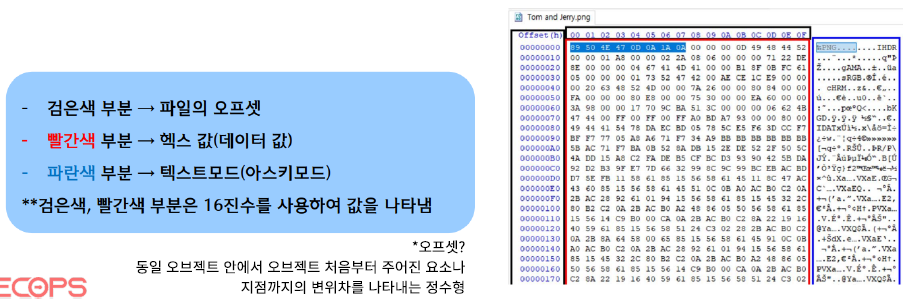
HxD 사용법
- HxD는 Hex 값 확인, Hex 값 변경, 파일 시그니처 확인 등 여러 목적으로 쓰이고 있는 도구로, 파일에 대한 데이터 값을 볼 수 있도록 하는 프로그램


4. 이미지 변조
- 이미지 파일 1개 준비
- 텍스트 파일을 압축하여 .zip 파일 1개 준비
- copy /b img,jpg+text.zip result.jpg